- Home
- SMB Cloud
- DomainsOn Sale
- Intl DomainsOn Sale
- Web HostingOn Sale
- Virtual Private ServerUpdated
- Dedicated ServersUpdated
- SSL CertificatesOn Sale
- Website Security Recommended
- Website MarketingGrow Biz
- Tally CloudSuper Hot
- SMB Cloud Desktop Work From Home
- Cloud DriveShare Files
- Cloud Password ManagerNew
- Secure Web AccessRecommended
- Acronis Cyber ProtectSecure Users
- DSC CertificatesSale
- Cloud Infrastructure
- Performance Cloud Most Popular
- Enterprise Cloud Updated
- Bare Metal CloudNew
- GPU CloudNew Plans
- HPC CloudNew Launch
- Virtual Private CloudUpdated
- Dedicated Private CloudUpdated
- Multi Cloud New
- Global CloudNew Locations
- Cloud PaaSNew Launch
- Cloud ContainersNew
- Cloud DatabasesNew
- Hybrid CloudUpdated
- Cloud Render FarmPublic Beta
- Cloud FaaSPrivate Beta
- Cloud I0TPrivate Beta
- Managed Colocation New DC's
- Cloud Productivity
- Business E-MailUpdated
- Microsoft 365 New
- G-Suite
- Cloud DesktopSuper Hot
- Cloud Conferencing
- E-mail Archiving Unlimited Storage
- Email Encryption
- Digital Signatures
- E-mail Security
- Email Signatures
- Cloud PBXComming Soon
- Cloud Contact CenterComming Soon
- Cloud Data Protect
- File-as-a-Service New
- Backup-as-a-ServiceHot
- DR-as-a-Service Updated
- Storage-as-a-Service
- Archive-as-a-Service
- Cloud Networking
- Security Services
- Cloud Security
- Managed Security
- Detect & Respond
- Security Posture Assessment
- Team Assessment
- Managed Security Monitoring
- Managed Security Operations
- Managed Incident Response
- Microsoft 365 Security
- Azure SecurityNew
- AWS Security
- Security Consulting
- Virtual CISO
- ISO Process Consulting
- GDPR Consulting
- SOC1 SOC2 SCOC3 Compliance
- PCI DSS Compliance
- HITECH Consulting
- Blockchain Consulting
- ISAE 3402 Assessment
- Microsoft SSPA Attestation
- SOC for Cybersecurity Assessment
- Agreed Upon Procedures Assessment
- HIPAA/HITECH Assessment Services
- HITRUST Assessment Services
- ISO 9001 Certification Services
- PCI DSS Assessment Services
- Security Ratings
- Assurance Exchange
- Security Training
- Security Hardware
- Managed Services
- Managed Sysadmin Services
- Cloud Consultation
- Cloud Monitoring
- Managed Cloud
- Managed Backup Service
- Managed Database Service
- Managed DevOps
- Managed Kubernetes
- Managed Webmaster Services
- Managed Remote Infra
- Managed Implementation Services
- Migration-As-a-Service
- Server Migration Service
- Mail Migration Service
- Database Migration Service
- Active Directory Migration
- Application Migration Service
- File Migration Service
- Archive Migration
- VMware Migration to Public Cloud
- Migrate To AWS
- Migrate To Azure
- Desktop Migration Service
- Teams Migration
- Free Azure Migration
- Free AWS Migration
- Cloud Training
- Strategic Consulting
- Cloud Apps
- Cloud Solutions
- Digital Transformation
- By Business Challenge
- Addressing Regulatory Requirements
- Consolidating Data Centers
- Controlling IT Spend
- Delivering Software as a Service
- Ensuring Business Continuity
- Maximizing Uptime & Performance
- Migrating to the Cloud
- Modernizing Application
- Outsourcing IT
- Protecting Business Data
- Scaling My Business
- Transforming My IT
- By Industry
- By Role
- By Initiative
- By Category
- By Vendors
- Microsoft-as-a-Service
- Acronis-as-a-Service
- Citrix-As-a-Service
- Citrix Workspace
- Citrix Virtual Apps and Desktops
- Citrix Content Collaboration
- Citrix Endpoint Management
- Citrix Managed Desktops
- Citrix Hypervisor
- Cirtix Sharefile
- Citrix ADC
- Citrix Application Delivery Management
- Citrix Gateway
- Citrix Intelligent Traffic Management
- Citrix SD-WAN
- Citrix Web App Firewall
- Citrix Analytics
- Crowdstrike As a Service
- Falcon Prevent (Next-Generation Antivirus)
- Falcon Insight (Endpoint Detection & Response)
- Falcon Device Control (Device Control)
- Falcon Overwatch (Managed Threat Hunting)
- Falcon Discover (IT hygiene)
- Falcon Spotlight (Vulnerability Assessment)
- Falcon X (Threat Intelligence)
- Falcon Search Engine (Malware Search)
- Falcon Sandbox (Automated Malware Analysis)
- VMware-As-a-Service
- Veeam-As-a-Service
- Redhat-As-a-Service
- Nutanix-As-a-Service
- LogMeIn-as-a-Service
- Rapid7-as-a-Service
- Rubrik-as-a-Service
- Splunk-as-a-Service
- Commvault-as-a-Service
- Sophos-as-a-Service
- Accops-as-a-Service
- NetApp-as-a-Service
- Soniwall-as-a-Service
- Trendmicro-as-a-Service
- Fortinet-as-a-Service
- PaloAlto-as-a-Service
- Bitdefender-as-a-Service
- By Use Case
- Solution Diagram
- Cloud Partners
- Support
- Insights
- About Us
- Our Team
- Customer Testimonials
- Events
- Careers
- Achievements
- Accreditations & Certifications
- Cloud Architecture
- Security Architecture
- Trust Center
- Legal
- Report Abuse
- Deals & Offers
- Contact Us
- Technology Partnerships
 +91-22-40074555 | Ext.1
+91-22-40074555 | Ext.1

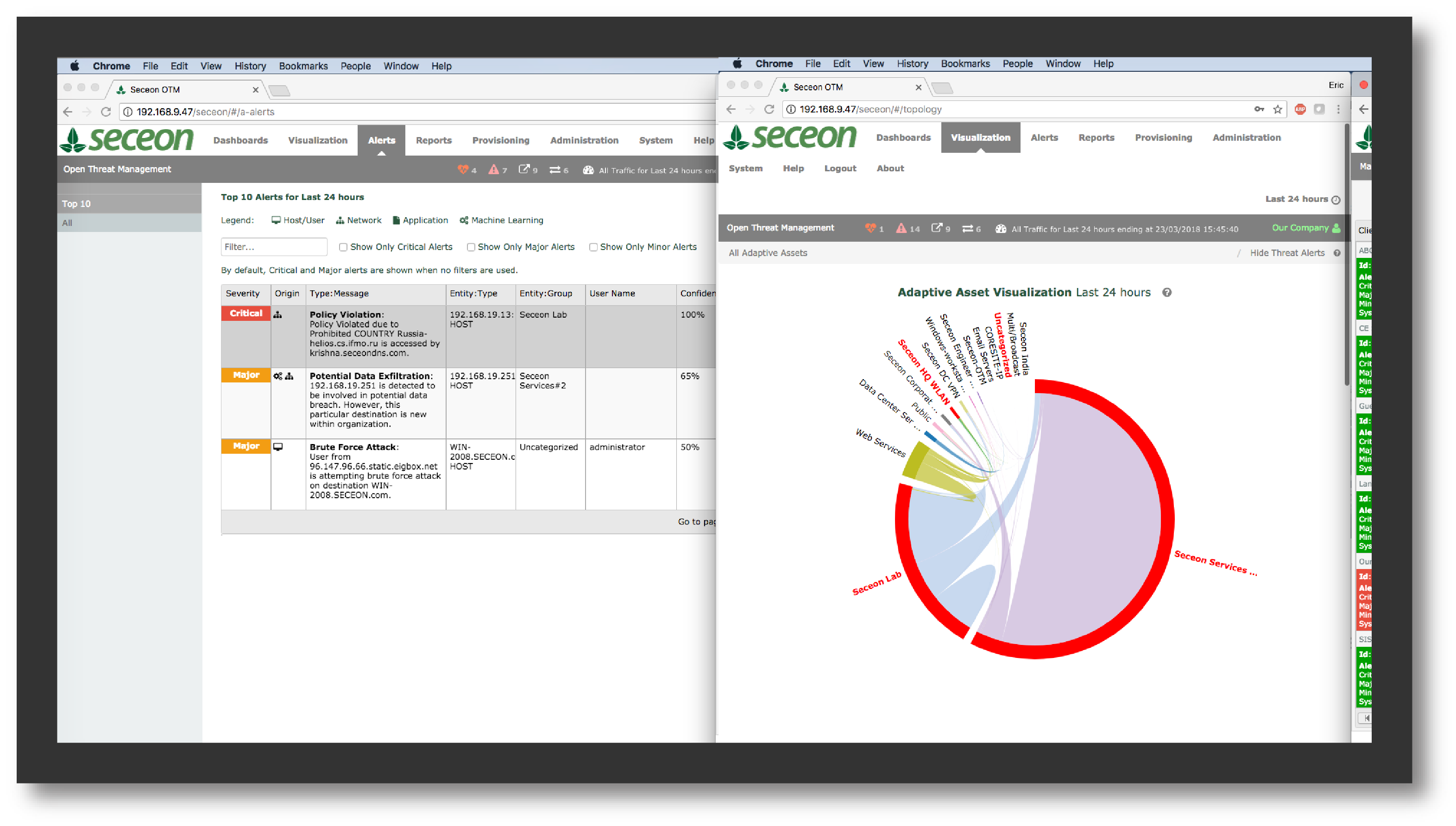
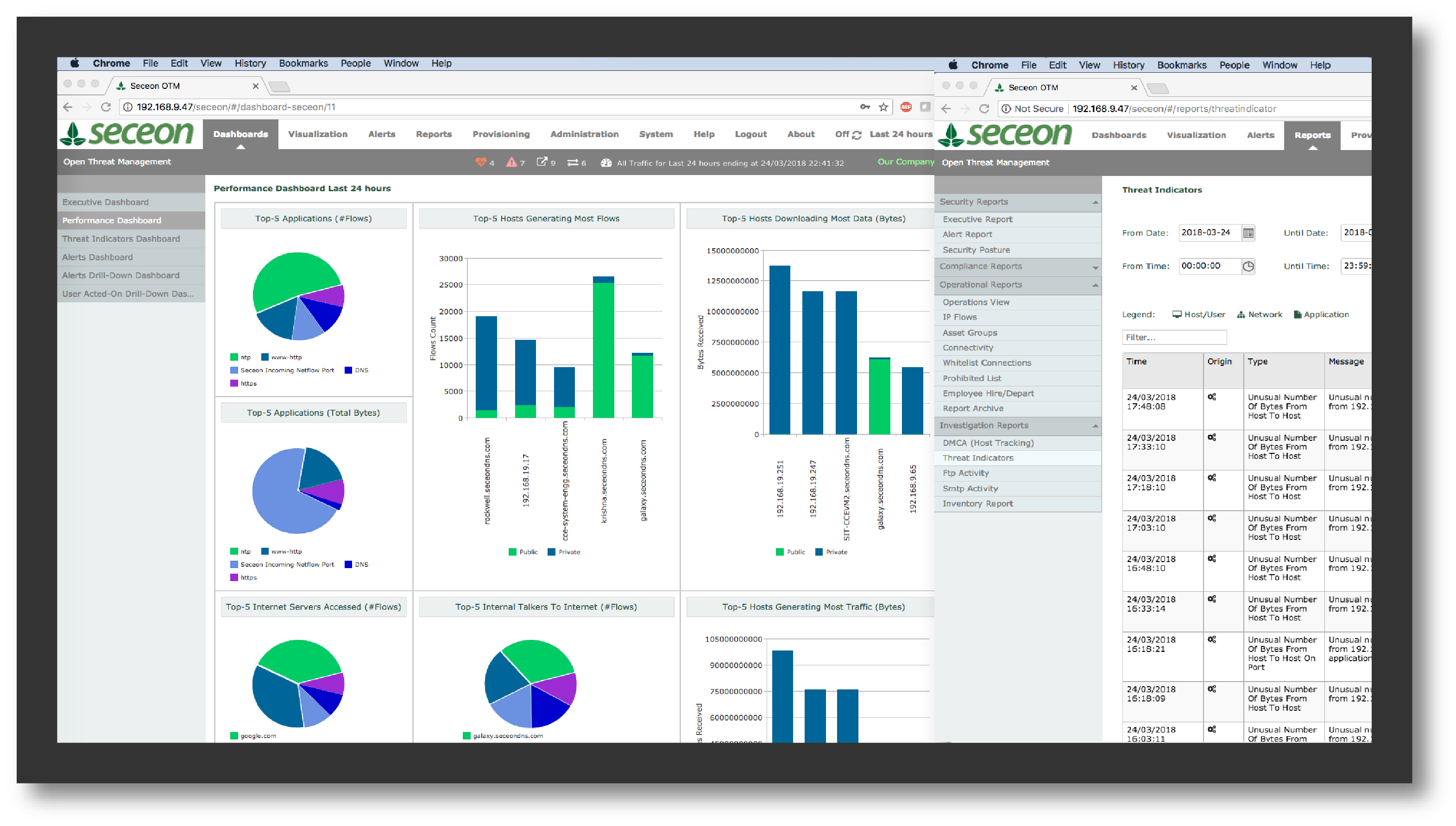






.png)