b440.png?height=70&name=onoff%20(1).png)
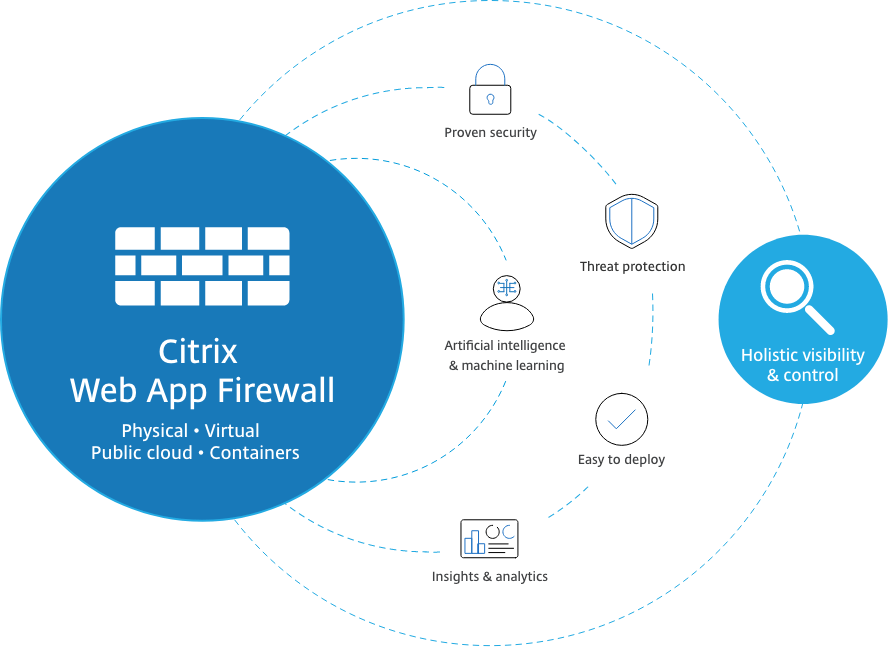
Multi-Cloud Holistic Security Framework
Xcellhost offers a single source of control for the security of websites, applications, and APIs, hosted across multiple cloud environments.
dfce.png?height=60&name=meter%20(1).png)
Built for Performance
Our web application firewall sits on the same Anycast network that powers our global CDN, HTTP/2, and web optimization features.
635d.png?height=60&name=daller%20(1).png)
Affordable, flat pricing
Xcellhost will never bill you for bandwidth spikes. We charge a flat rate based on your plan, so you can rest easy.
3f37.png?height=60&name=settings%20(1).png)
Automatic WAF Updates
When we find threats that apply to a large portion of our users, we automatically apply WAF rules
 +91-22-40074555 | Ext.1
+91-22-40074555 | Ext.1